After a lot of stopping and starting and mis-communication between me and my developer (a java expert).
We have decided to reduce the scale of this phase so as to meet the Halloween deadline.
The tracker is now going to be done in server-side code on tomcat.
Ruby on Rails website has now been delayed to next phase.
Also, the project team is now three as we have been joined by a Style, Art and Editorial Director, Trine (from Norway) adding to the currrent team of me, Project Production Manager (from Jamaica) and Vicent, Project Developer (from China).
Here in the Developer's words is how the tracker works,
Proposed Ruby on Rails (RoR) Website before it was delayed:
Core website: I set up 3 tables, called users, catelogs, swarms.
Users is used to record a user's connection.
Catelogs is used to save catelog information.
Swarms is used to save swarm information (including corresponding catelog_id and last-time connect in seconds).
I then use RoR to make some function, such as browse catelog, browse swarms by catelog_id, show swarm by swarm_id and count users by swarm_id.
Tomcat:
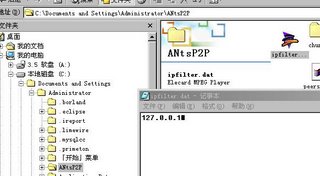
I use java/jsp to let user download core_basic.jar file, and use java to output ipfilter.dat.
I have tell you that because of the deadline is closer, so I just use java to work now, later, I wanna use RoR totally instead of tomcat.
This why I use java to output the ipiflter.dat.
I also use tomcat/java to update the time that user last time download ipfilter.dat.
just the user whose ip address is in the ipflter.dat can join the swarm.
I take the "5" as swarm_id, then I find the ip addresses of users whose swarm's id is "5" from users table in database.
When I gather their ip addressess, I output the ip addresses as a file called ipfilter.dat to user for their download.
See picture above.





